Transactional security can be enhanced by employment of a second authentication factor, “what you have.” This authentication factor is typically deployed in conjunction with the first authentication factor (i.e., two-factor authentication), such that a user must typically establish his or her identity both by using a username/password (what the user knows) and by confirming his or her identity through use of an object (what the user has). This second authentication factor may be implemented through a variety of measures, including use of hardware tokens (small electronic devices) that generate a number that a user must enter to complete the authentication process. As typically implemented, the number provided by a hardware token expires after a given period (e.g., 30 seconds or a minute) and is replaced by a new number. Even if a fraudster has obtained a user’s username and password, the fraudster will generally be unable to access the user’s account without also having obtained the user’s hardware token. More recently, software tokens (e.g., apps for smartphones and other mobile devices that generate a number for the user to enter) may take the place of dedicated hardware tokens.
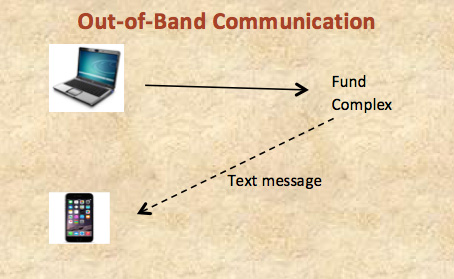 Mobile devices may also be used to implement two-factor authentication over separate communication channels, or out-of-band communications. For example, because most mobile phones permit text messaging, financial institutions can utilize out-of-band communications—such as text messages containing numbers, one-time passwords, or details of a transaction—to their online customers, either as part of the initial authentication process or as confirmation of a particular transaction request. Customers, in turn, may be required to enter these numbers or one-time passwords, or to confirm the texted details of the transaction.1 Experts believe that the use of two separate channels of communication provides significant additional security over the use of a single channel.2
Mobile devices may also be used to implement two-factor authentication over separate communication channels, or out-of-band communications. For example, because most mobile phones permit text messaging, financial institutions can utilize out-of-band communications—such as text messages containing numbers, one-time passwords, or details of a transaction—to their online customers, either as part of the initial authentication process or as confirmation of a particular transaction request. Customers, in turn, may be required to enter these numbers or one-time passwords, or to confirm the texted details of the transaction.1 Experts believe that the use of two separate channels of communication provides significant additional security over the use of a single channel.2Back