Fund groups typically take strong steps to ensure that online transaction systems are protected, both from external and internal threats, through appropriate network security measures. Moreover, these online transaction systems are generally segregated from other computer systems through the use of firewalls and/or DMZs (i.e., firewall-protected servers that are set up in the “demilitarized zone” outside the perimeter of a corporate network). A full discussion of relevant network security measures for online transaction systems is beyond the scope of this study, but has been described in greater detail in ICI Mutual’s prior risk management studies on computer security, identity theft, and digital age risks.
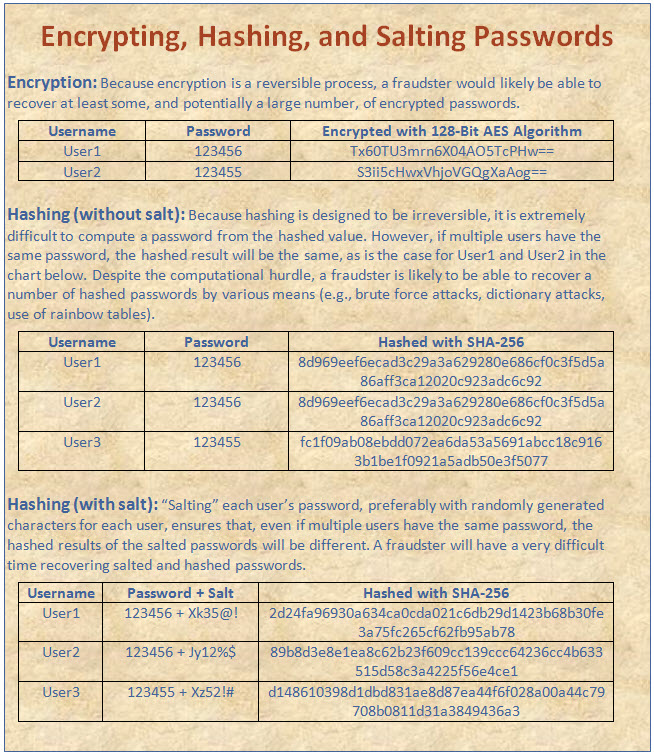
Fund groups also take steps to protect authentication-related information that is stored on online transaction systems. While storing passwords in plain text creates an obvious vulnerability, merely encrypting them, as was the case in Adobe’s 2013 data breach (in which over 150 million records were breached), still leaves a significant vulnerability.1 (Because encryption is designed to be a reversible operation, a fraudster obtaining a list of encrypted passwords would likely be able to recover at least some of those passwords.) To address this vulnerability, fund groups tend to store passwords that have been “salted” (i.e., additional characters are added to the passwords) and then “hashed” with an algorithm that is designed to be irreversible. Salting and hashing passwords (preferably with a slow hashing algorithm, thus increasing the amount of time needed for a successful brute force attack) makes it significantly more difficult for a fraudster to recover passwords.2
Back