While strong authentication measures may significantly reduce the risk of fraudulent transactions by unauthorized persons, it is important to recognize the limits of authentication. Even the strongest authentication measures cannot completely eliminate the potential for fraudulent transactions.1
 A fraudster may defeat authentication measures by compromising the systems of a financial institution (whether through hacking, social engineering, or otherwise) and causing transactions to be initiated. It was recently reported that dozens of banks and other financial institutions suffered losses estimated to be in excess of $300 million and perhaps as high as $1 billion after their systems were compromised through spear phishing e-mails sent to employees. Once the systems were compromised, the cybercriminals opened fraudulent accounts, transferred money to fraudulent accounts, and caused ATMs to dispense cash at given times and locations.2
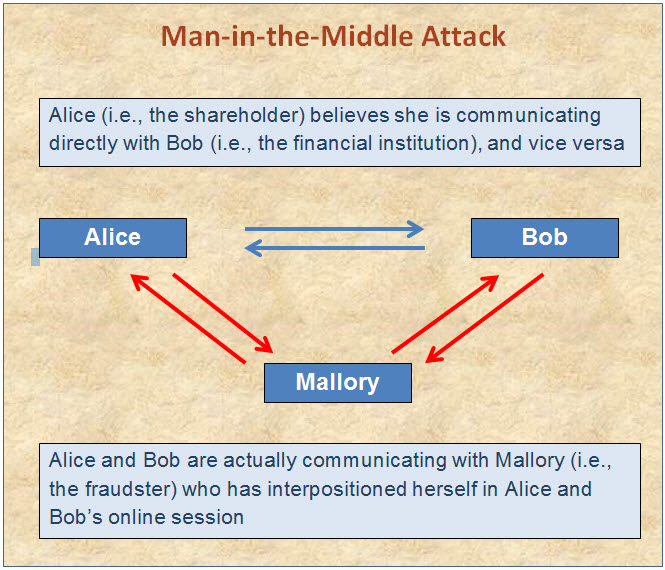
A fraudster may defeat authentication measures by compromising the systems of a financial institution (whether through hacking, social engineering, or otherwise) and causing transactions to be initiated. It was recently reported that dozens of banks and other financial institutions suffered losses estimated to be in excess of $300 million and perhaps as high as $1 billion after their systems were compromised through spear phishing e-mails sent to employees. Once the systems were compromised, the cybercriminals opened fraudulent accounts, transferred money to fraudulent accounts, and caused ATMs to dispense cash at given times and locations.2A fraudster may also defeat authentication measures by otherwise circumventing them. As one cybersecurity expert noted a decade ago, two-factor authentication may be defeated by a man-in-the-middle attack or a Trojan attack.3 In a man-in-the-middle attack, a fraudster “hijacks” an online session in which a user has already been authenticated by an organization. Because the fraudster is impersonating both the user (to the organization) and the organization (to the user), neither party may be aware that the session has been hijacked. In the Trojan attack, the fraudster installs malware on the victim’s computer; once the victim logs in to his or her financial account, the fraudster may either use the properly authenticated session to conduct fraudulent transactions or gather the user’s credentials to conduct fraudulent transactions at a later time.4
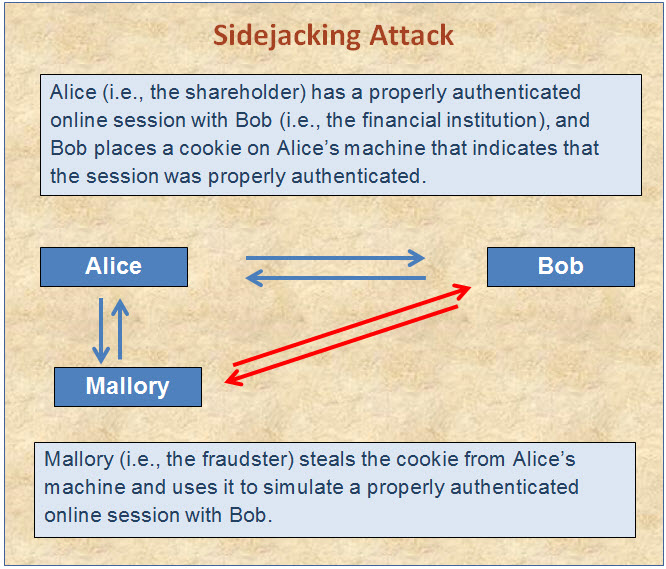 An exposed vulnerability of a commonly used blogging tool illustrates another means of circumventing authentication measures (called a sidejacking attack).5 In this case, the blogging tool provided its users with the option of using two-factor authentication, which should provide a high level of security. Once a session was authenticated, a cookie was placed on the user’s machine. However, this cookie was not encrypted and could be copied to another machine. A fraudster with access to the user’s computer (e.g., if the user were using an unsecured WiFi “hotspot”) could then copy the cookie and impersonate the user.6 This form of attack has been referred to as “sidejacking” the session.
An exposed vulnerability of a commonly used blogging tool illustrates another means of circumventing authentication measures (called a sidejacking attack).5 In this case, the blogging tool provided its users with the option of using two-factor authentication, which should provide a high level of security. Once a session was authenticated, a cookie was placed on the user’s machine. However, this cookie was not encrypted and could be copied to another machine. A fraudster with access to the user’s computer (e.g., if the user were using an unsecured WiFi “hotspot”) could then copy the cookie and impersonate the user.6 This form of attack has been referred to as “sidejacking” the session. Back